Summary
Cyber insurance is moving from paying for damage to validating resilience before damage occurs. Insurers no longer want assurances. They want evidence.
Research explains why. Today’s insurer questionnaires rarely measure true technical maturity. While many CIS Controls are referenced, only 6 to 35 percent are assessed in meaningful depth. The result is predictable: mispriced policies and weak risk differentiation.
The market is now shifting toward Cyber Insurance 3.0. Static reports are being replaced by continuous measurement. Zero Trust, live telemetry, and real-time dashboards are becoming the new underwriting foundation.
Zero Trust makes risk visible and controllable. When implemented effectively, it can reduce breach costs by up to 75 percent and gives insurers measurable proof that security controls actually work.
Organizations that can demonstrate continuous governance and validated security controls are rewarded. Lower premiums. Greater trust from regulators. And stronger operational resilience when incidents occur. Cyber insurance is no longer just a financial backstop. It is becoming a reflection of how mature an organization’s cyber resilience truly is.
A Market at an Inflection Point
Cyber insurance is at a breaking point. What started as a financial hedge after an incident is becoming a mechanism to manage risk before it materializes. The shift is clear: from reimbursement to rewarding verifiable resilience.
Two forces are driving this change.
- First, Zero Trust has matured. It is no longer a conceptual model, but a practical and measurable strategy for risk control.
- Second, academic research is exposing a growing misalignment between insurance requirements and actual risk reduction. Insurers ask many questions, but too often not the right ones.
Recent research makes this gap visible. The study Mapping Cyber Insurance Questionnaires to Standardized Security Controls offers the most detailed view to date of how cyber insurers assess risk.
Led by Steve Bielen, Senior Information Security Officer at Vanbreda Risk & Benefits, the research systematically mapped twelve underwriting questionnaires from major European insurers against the CIS Critical Security Controls.
The conclusion is uncomfortable, but unmistakable. The alignment between what insurers ask and what truly reduces cyber risk remains incomplete, inconsistent, and frequently superficial.
For underwriters, this leads to mispriced risk.
For CISOs, it means investments that are poorly recognized. That tension is why the market has reached an inflection point.
From Information Asymmetry to Assurance
Cyber insurance faces a familiar economic problem. Information asymmetry. Rothschild and Stiglitz described it in 1976. When insurers know less about risk than the insured, adverse selection follows. High-risk organizations dominate the pool. Premiums rise for everyone.
Research shows why this asymmetry persists. Insurers still rely on questionnaires that are poorly aligned with recognized cybersecurity frameworks. Across the insurers studied, coverage of the CIS Controls ranged from 55 to 94 percent. Actual implementation depth ranged from just 6 to 35 percent.
The implication is clear. Many of the right questions are asked, but only very few assess whether controls are effective, mature, or consistently enforced.
This is not an academic nuance. Poor alignment undermines underwriting accuracy. Insurers struggle to price risk correctly. Organizations remain uncertain about what is truly required of them.
Breaking this cycle requires a structural shift. Underwriting must move from checklists to control validation. From asking whether a policy exists to confirming that safeguards such as multifactor authentication, segmentation, and incident response are actively enforced and monitored.
To close the knowing–doing gap, insurers must move beyond questionnaires toward real-time telemetry of fundamental security controls.
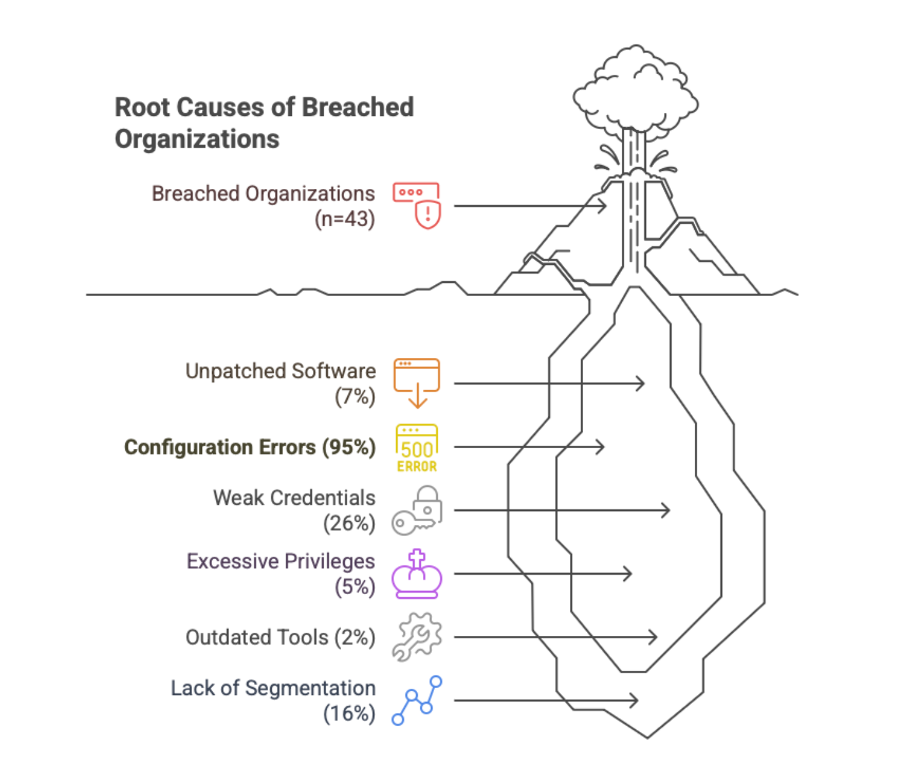
The evidence is overwhelming. Over the past twenty years, 95 percent of the root causes of major incidents can be traced back to configuration flaws. These are preventable technical errors, detectable through configuration logs. On top of that, they’re measurable against established best practices. And correctable in real time.
The analogy is straightforward. If a CCTV camera fails, the monitoring center sees it immediately. No questionnaire is required.
The results and practical lessons of this analysis into the knowing–doing gap were published in the ISACA Journal and are visualized in Figure 1.
Zero Trust: The New Currency of Insurability
Decoding the Future of Cyberinsurance, a New York–based roundtable on Zero Trust in the financial sector, revealed a clear shift in industry thinking. Zero Trust is increasingly recognized as the missing link between security operations and financial assurance.
During the roundtable discussions, participants converged on the same conclusion. Zero Trust is no longer optional. It has become the operational backbone of measurable cyber maturity. The same conclusion was reinforced during the Group Support System session in July at Venable.
The logic is straightforward. Zero Trust focuses on protect surfaces, continuous verification, and least privilege. These principles map directly to the variables that matter most to cyber insurers: the likelihood of loss and the impact when incidents occur.
Traditional controls cannot demonstrate effectiveness in real time. Zero Trust as a Service can. By integrating technical controls with continuous telemetry, dashboards, and tested incident response, ZTaaS provides empirical evidence of resilience. Supporting research by Tim Timmermans (CISO the Netherlands ON2IT) and myself shows the financial effect. Zero Trust as a Service can reduce breach costs by up to 75 percent. At the same time, it enables lower insurance premiums by demonstrating stronger governance and higher incident readiness.
Key Findings Shaping the Future of Cyber Insurance
1. The Disconnect Between Frameworks and Practice
The research exposes a structural imbalance. Most insurers assess preventive controls such as firewalls and antivirus software. Very few evaluate Respond and Recover capabilities, the functions that ultimately determine loss severity.
This reflects a bias toward prevention over resilience. Future underwriting must incorporate response-based controls, as these directly affect recovery time, regulatory exposure, and reputational damage.
2. Revenue-Based Risk Pools Are Obsolete
Segmenting insured organizations by annual revenue remains common practice. It is also a poor proxy for cyber risk.
Empirical research shows that industry type and operational exposure are far stronger predictors of loss. Manufacturing, healthcare, and financial services each face distinct threat models and should be assessed accordingly.
Risk-driven segmentation using protect surface definitions and Zero Trust maturity scores enables fairer premiums and more sustainable risk pools. This approach, including critical success factors and failure modes, is detailed in the 2022 paper Perspectives from 50+ Years’ Practical Zero Trust Experience and Learnings on Buyer Expectations and Industry Promises.
3. Zero Trust as a Shared Framework for Insurers and Insured
Both the research led by Bielen and ON2IT’s market validation in the United States point to the same need: a shared language between insurers and insureds.
Standardized frameworks such as the CIS Controls and NIST CSF provide that foundation. Aligning underwriting questions to these controls improves transparency for organizations and enables comparability across insurers.
4. Dashboards as the New Audit Interface
As highlighted during the New York roundtables, dashboards are replacing traditional compliance reports as the primary evidence layer for assurance.
Real-time visibility into asset inventories, control effectiveness, and incident metrics provides underwriters and regulators with continuous proof of security posture, rather than static attestations after the fact.
5. From Reactive Payouts to Preventive Incentives
The trajectory is clear. Cyber insurance is shifting toward incentivizing continuous validation.
Premium discounts and extended coverage will increasingly be tied to validated Zero Trust adoption, mirroring how automotive insurers reward telemetry-based safe driving.
Cyber insurance is moving upstream. From paying for failure to rewarding proven control.
The Road Ahead: Cyber Insurance 3.0
Cyber Insurance 3.0 is taking shape. In this model, the policy is no longer just a financial instrument. It becomes a mechanism for governing cyber risk.
Insights from leaders across insurance, technology, and finance point to a consistent set of changes. In the 3.0 model:
- Underwriting is informed by real-time security telemetry, sourced from CISO teams or Managed Security Service Providers.
- Premiums are dynamically priced based on the measured risk posture per protect surface, reflecting differences in asset value, exposure, and required security levels.
- Claims are assessed using dashboard-based evidence, not post-incident declarations.
- Policy renewals depend on continuous compliance with Zero Trust metrics, not periodic attestations.
This shift requires insurers to invest in new actuarial models. These models must directly link Zero Trust maturity and telemetry data to claim frequency and severity. The result is a move from uncertainty to quantifiable risk management.
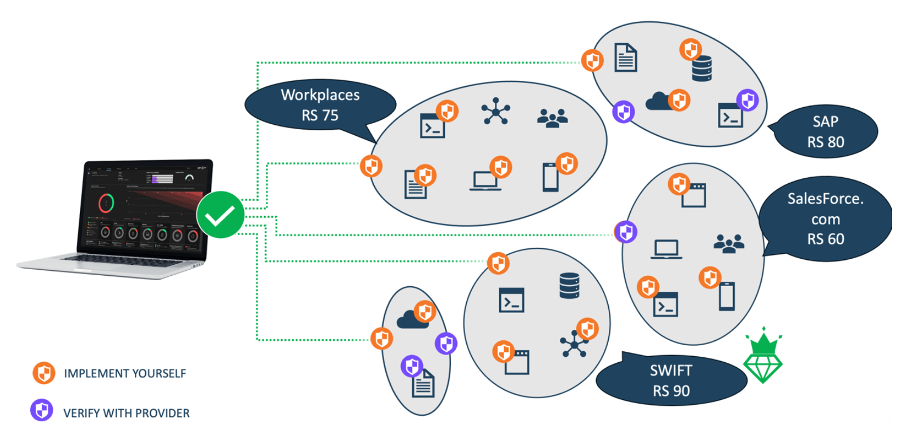
Importantly, this is not a future vision. The required 3.0 models, data ingestion pipelines, and visualizations already exist. Figure 2 illustrates a working example in the form of the AUXO platform, where real-time event and configuration log data is used as actuarial evidence.
Combined with insurers’ underwriting expertise, Cyber Insurance 3.0 moves from concept to operational reality.
Conclusion: The Path to Assurance
The future of cyber insurance will not be decided by policy language, but by proof of control.
Research provides the quantitative foundation. Decoding the Future of Cyberinsurance, the New York–based roundtable, provides the qualitative direction. Together, they point to a market moving toward data-driven assurance built on Zero Trust.
In this model, insurers become more than financiers of recovery. They become enablers of resilience.
Organizations that can continuously and measurably demonstrate control effectiveness will be rewarded. With lower premiums. With stronger trust from regulators and investors. And with greater operational resilience.
Cyber insurance will no longer reward those who survive incidents.
It will reward those who prevent them.
A shift to real-time, telemetry-based underwriting using Zero Trust and continuous validation.
They align with CIS Controls on paper but measure true technical maturity in only 6–35% of cases.
It provides measurable evidence of control effectiveness and can reduce breach costs by up to 75%.
Industry type, protect surfaces, and operational exposure correlate far better with loss likelihood.
Through dashboards showing live asset inventories, configuration health, and incident metrics.
Lower premiums, better governance, stronger investor confidence, and improved resilience.


