Managed security services
Incident Management
Rapid response to incidents with a multidisciplinary team of experts
Zero Trust as a strategy focuses on prevention, but no strategy can ever prevent 100% of events. In case of any incidents, we seek to minimize the adverse impact of incidents and, after an incident has already taken place, we seek to prevent incidents from happening again.
Depending on the severity of an incident, a team will be appointed to deal with specific incidents. Our teams are trained to work with established protocols and checklists to maintain data integrity during and after an incident.
We follow a set number of steps when an incident occurs:
Identify a potential problem (including proper prioritization).
Systematic investigation, resulting in a Root Cause Analysis.
Identification of change(s) needed to resolve the problem.
Once changes have been implemented, verify that the problem has been resolved. Verification must be done by both ON2IT and the customer.
Problem closure.
unique security features
Optimize your cybersecurity posture with AUXO™

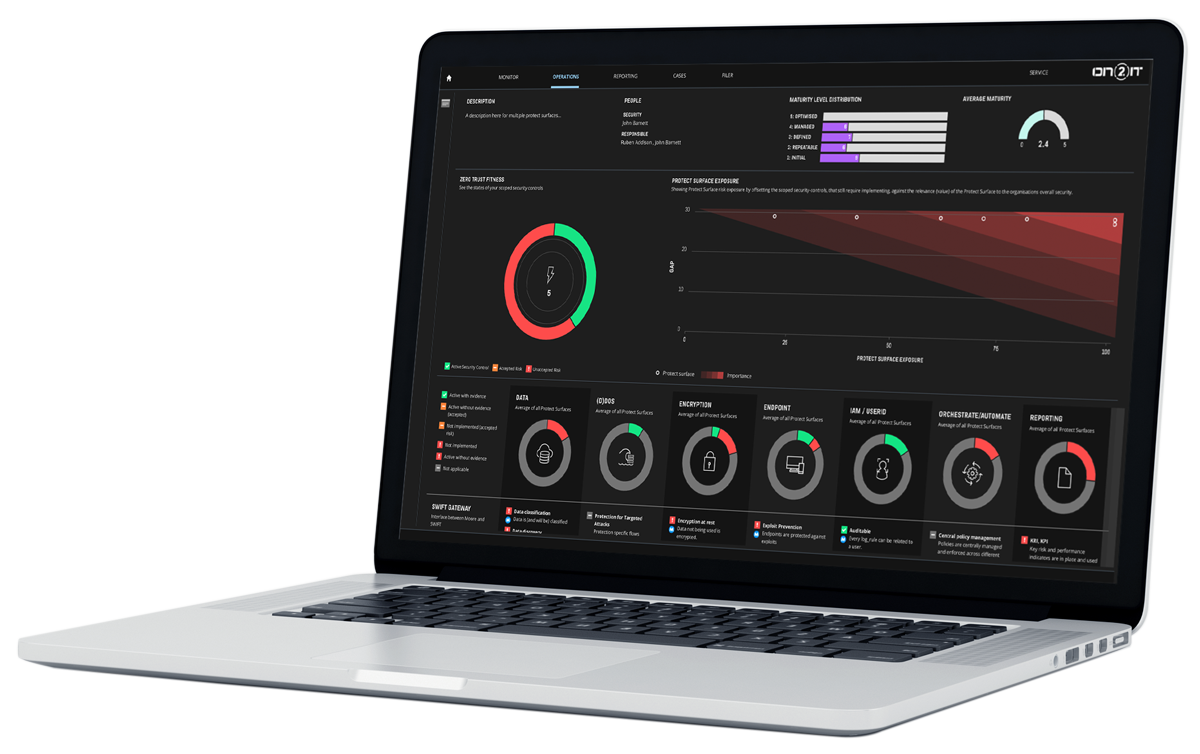
Protect Surface Management
Prevent data breaches with our Zero Trust Protect Surface Management

Incident Management
Rapid response to incidents with a multidisciplinary team of experts

Improvement Management
Continuous learning from events while enriching policies and configurations

Compliance Management
Real-time overviews and 24/7 access to information needed for compliance


