For years, the Purdue Model has been the standard framework for securing Operational Technology (OT) environments, offering a structured approach to segmentation. However, as cyber threats evolve and the IT-OT convergence accelerates, the model is increasingly seen as outdated. Meanwhile, Zero Trust has emerged as a leading security strategy in IT.
With increasing threats targeting industrial control systems, and the convergence of IT and OT networks, improving OT security is no longer optional: it’s a necessity.
Can Zero Trust be effectively applied to OT as well?

What is the Purdue Model and how does it work?
The Purdue Model is a well-known framework in OT security, though it may be less familiar to IT professionals. It’s worth pointing out that it shares similarities with how segmentation has historically been implemented in IT environments.
At its core, the Purdue Model divides infrastructure into different levels:
- Level 0 (Process): Sensors
- Level 1 (Control): PLCs (Programmable Logic Controllers)
- Level 2 (Supervisory): HMI (Human-Machine Interface)
- Level 3 (Operation): Historian
- Level 4 (Enterprise): Remote Access Server
- Level 5 (DMZ): Web Server
There’s a lot here that IT professionals will recognize. The traditional network segmentation is apparent and the DMZ and Enterprise layers are familiar. Similarly, the three-tier segmentation approach used in IT (Web, Application, and Database servers) can be loosely mapped to different Purdue levels. Luckily this segmentation method is not often used, seeing as it has the same flaws as the DMZ model.
Why the Purdue Model falls short in OT security
While the Purdue Model itself is not inherently flawed, its practical application introduces security challenges. These challenges don’t differ from those faced in IT security today (see The Broken DMZ Model).
The main issue is that levels within the Purdue Model are often too broad, grouping all sensors in Level 0, all PLCs in Level 1, and so on. This broad segmentation creates several security risks:
- Expanding attack surfaces: Increased automation results in more OT devices, widening the attack surface and increasing the blast radius of potential breaches.
- More intelligent OT devices: Devices now extend beyond their basic functions, increasing exposure to cyber threats. Think of network-connected torque wrenches for example.
- Blurring of control and operation layers: Some OT devices combine control and operation functions, making strict segmentation difficult.
- IP connectivity: More OT devices are connected via IP networks (e.g., Modbus over IP), making them more accessible and vulnerable.
Additionally, many OT environments lack basic cybersecurity measures such as encryption, leaving them highly susceptible to attacks.
Zero Trust: Principles and benefits for OT
Zero Trust follows the principle of ‘never trust, always verify’ and is built on four core principles:
- Design from the inside out: Security should start at the most critical assets and expand outward.
- Focus on business outcomes: Protection should align with business needs.
- Who and what needs access: Access should be strictly controlled and monitored.
- Log and inspect all traffic: Continuous monitoring is essential for detecting anomalies.
Failures in OT components often have immediate and severe business impacts, which makes Zero Trust’s focus on business outcomes particularly crucial to OT environments. As a strategy designed to prevent breaches and limit the damage if one does occur, Zero Trust is a great fit for OT security.
Applying Zero Trust to OT: A practical approach
Applying Zero Trust to OT environments requires shifting from broad segmentation (as seen in the Purdue model) to protect surfaces that define what is most critical to the business.
This approach views security not as horizontal layers (like Purdue) but as vertical columns mapped to specific business processes. Itʼs important to note that these protect surfaces do not necessarily span all or multiple levels. The goal is to segment based on business needs rather than rigid network architecture.
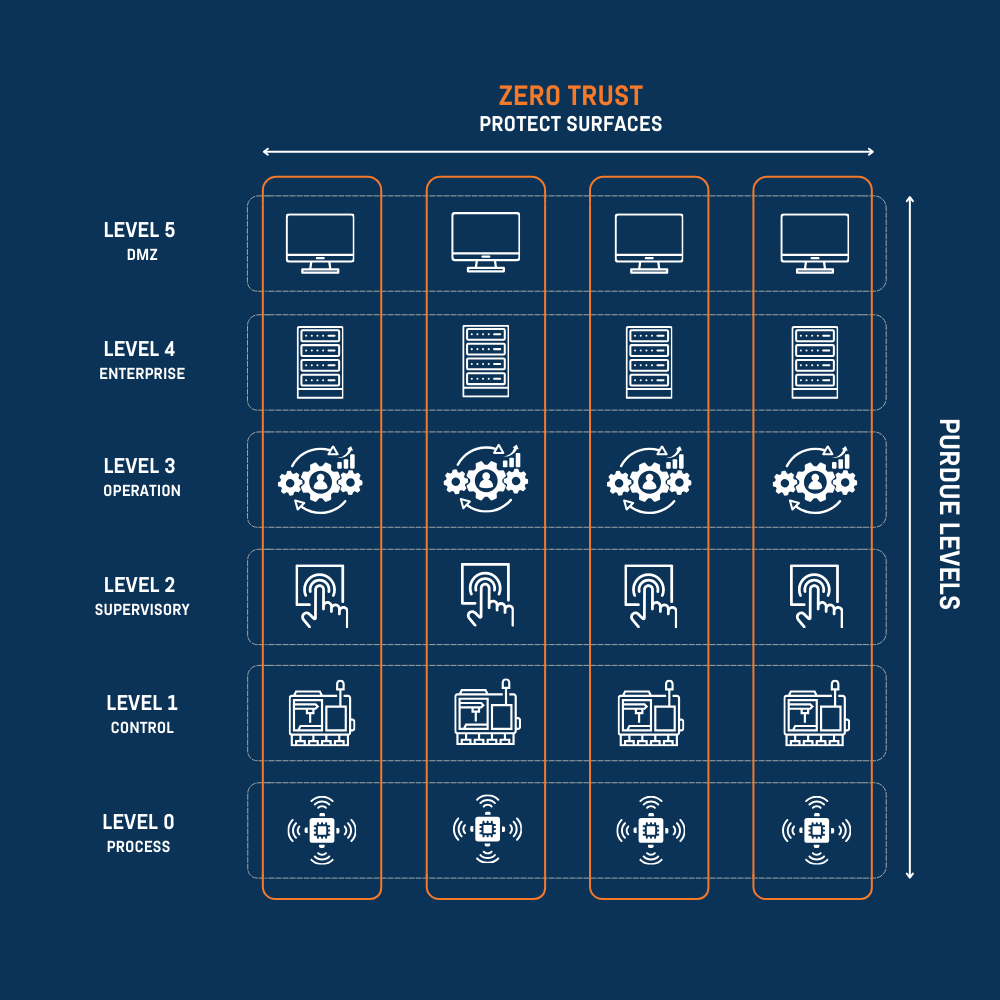
Protect surfaces in OT: How Zero Trust segments critical assets
In practice, Zero Trust can be applied to OT as demonstrated in the following examples:
- Instead of grouping all sensors into one big Level 0 domain, sensors controlling specific critical industrial processes should be segmented into a separate protect surface with strict access controls. This isolates them from other unrelated processes.
- Instead of treating all HMIs at Level 2 as equal, different HMIs should have dedicated security policies based on their function and business impact. For example, an HMI used for temperature monitoring should not have connectivity to a PLC managing robotic arms in a production line.
- Separation of Building Automation Systems (BAS) from Production Networks. Many industrial sites have HVAC, lighting, and energy management systems running on the same network as production lines. Zero Trust principles dictate that BAS should be segmented into its own protect surface(s), ensuring that a compromised smart thermostat doesn’t become an entry point into critical OT systems.
If applied correctly, Zero Trust and the Purdue Model would not compete with each other, but be complementary. Zero Trust enhances the Purdue Model by making it more granular, adaptive, and aligned with business objectives.
In IT environments, the relevance of DMZs has been questioned, particularly for data protection (see The Broken DMZ Model). However, in OT environments, it’s often about protecting devices rather than just data.
Thus, using the Purdue model within a Zero Trust framework remains relevant.
Overcoming challenges in Zero Trust for OT security
Implementing Zero Trust in OT is challenging but necessary. Key obstacles include:
- High operational risk when modifying critical infrastructure.
- Legacy systems that were not designed with security in mind.
- Diverse and outdated protocols, often proprietary or Ethernet based, but not IP.
- Distributed infrastructure, making enforcement difficult.
- Industry-specific constraints that affect feasibility and rollout.
Why Zero Trust works for OT security
The Purdue Model has long served as a foundation for securing OT environments, but its limitations in addressing modern cyber threats are evident. Zero Trust enhances OT security by enforcing strict access controls, continuous monitoring, and micro-segmentation.
While implementing Zero Trust in OT can be challenging due to legacy infrastructure and operational risks, the benefits far outweigh the difficulties. Improving OT security is no longer optional: it’s a necessity. By taking a phased approach and aligning security strategies with business objectives, organizations can achieve a more resilient, adaptive, and future-proof OT security framework.


