Summary
The walls between IT and OT already down.
What were once separate worlds with clear boundaries and distinct teams are now deeply connected. Operational technology increasingly depends on IT systems, while IT professionals must understand and operate within OT constraints.
The IT/OT convergence flips the script on security. Traditional models such as the Purdue Model were designed for separation. Today’s reality demands something different: a model that ditches static boundaries and kills implicit trust.
That’s where Zero Trust 2.0 for OT security comes in.
The evolution: from isolation to integration
Not long ago, OT environments were isolated islands.
Control systems ran independently, accessible only through dedicated workstations requiring physical presence. The factory floor and the IT department might as well have been on different planets.
That world is gone.
Today’s OT environments are connected. Remote access from IT workspaces to control systems is routine. And this is just the start. Modern industrial operations demand deeper integration:
- Predictive maintenance systems automatically monitor cycle counts- like how often a robot arm extends and retracts before maintenance is required.
- Early warning systems flag subtle malfunctions before they snowball into outage.
- AI-driven optimization monitors processes in real-time, identifying inefficiencies and suggesting fixes.
- Cloud analytics combine data across sites to give enterprise-wide visibility.
This isn’t the future.
This is now.
Driven by business demands for uptime, efficiency, and competitive edge – all pulled in from the IT side, deep into what was once OT-only territory.
IT vs. OT: Why IT and OT must learn a common language
The technical IT/OT convergence is hard.
The cultural clash is harder.
IT and OT still don’t speak the same language – and that disconnect creates risk.
The IT mindset
When IT professionals enter OT, they often bring assumptions that don’t hold:
- “We’ll patch this next week.”
In OT, maintenance windows are rare – and often measured in months or years. Critical production systems cannot simply be taken offline for updates. - “Let’s roll out security controls everywhere.”
IT controls can break critical OT equipment – sometimes permanently. - “Why isn’t this system updated?”
Updating a PLC can require regulatory recertification, test cycles, and millions in lost uptime.
The IT world moves fast. Dozens of changes a day is normal.
In OT, that pace is unthinkable.
The OT mindset
OT professionals must understand the IT world too:
- Regular patching and updates aren’t nice-to-haves – they’re baseline expectations.
- Security controls aren’t red tape – they’re protection in a connected world.
- Fast change cycles exist because the business demands agility.
In OT, availability is king.
Rule #1: Don’t break production.
That principle is non-negotiable. But it can’t excuse ignoring security.
Bridging the gap
Both sides are right – in their own world.
IT teams must accept that downtime in OT can be catastrophic.
OT teams must accept that in a connected world, security is survival.
Neither team needs to abandon its core values.
They need a shared framework.
The Purdue Model’s unintended legacy
If you read my last post on Purdue vs Zero Trust, you know the Purdue Model shaped OT security for decades.
But here’s the problem:
As IT and OT converge, the Purdue Model may be doing more harm than good.
It was built for separation.
Today’s world runs on integration.
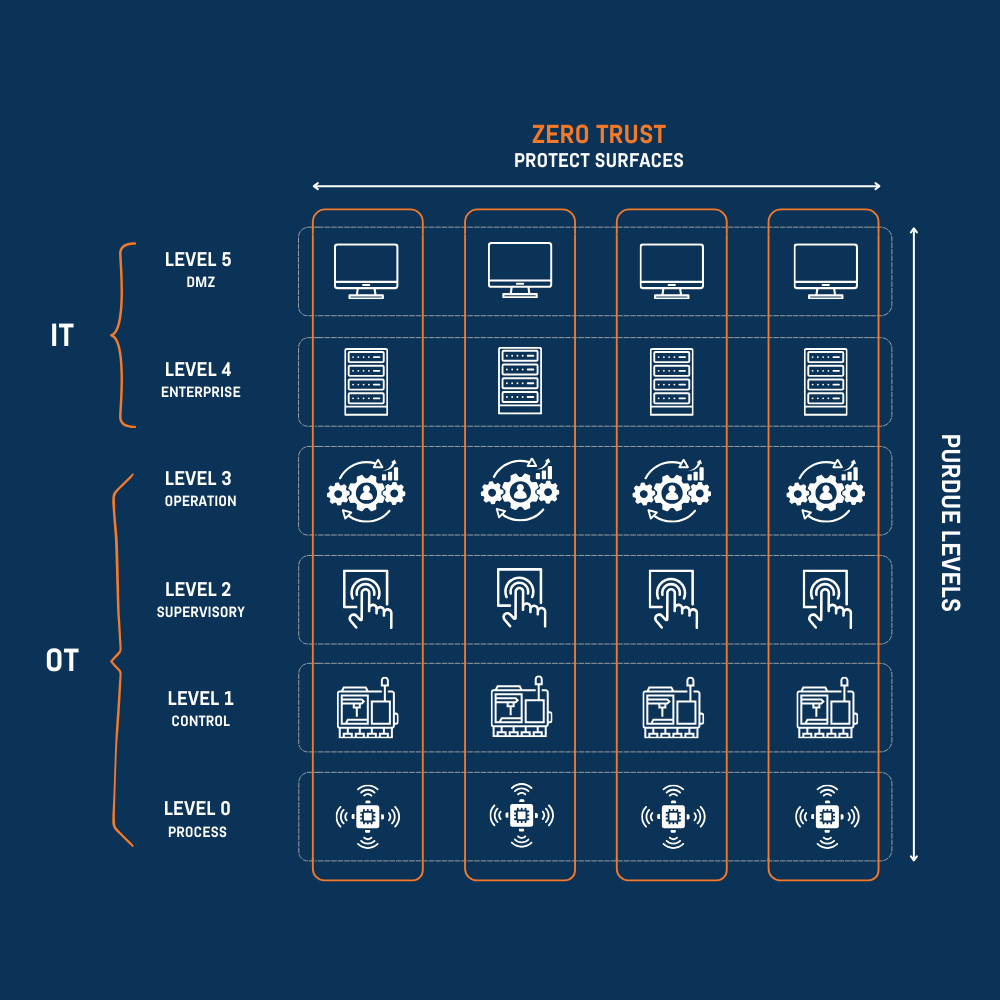
The traditional Purdue Model is shown as a stack of horizontal layers. Clear boundaries separate the IT domain at Levels 4 and 5 from the OT domain at Levels 0 to 3. This visual split reinforced the idea that IT and OT were fundamentally different.
But this isn’t just about network architecture.
The layered approach shaped thinking around responsibility and ownership:
- Separate teams with separate responsibilities
- Different security approaches per domain
- Minimal collaboration between IT and OT
- Distinct budgets and priorities
The Purdue Model didn’t create these divisions – but it normalized them.
And in doing so, it may have made today’s convergence harder than it needed to be.
Zero Trust 2.0: Vertical thinking for a horizontal world
Zero Trust for OT doesn’t mean throwing out the Purdue Model.
It means adding a new layer of thinking: vertical protect surfaces that cut across the horizontal stack.
The Purdue Model still provides useful horizontal segmentation – especially in OT security, where you’re securing devices, not just data.
But Zero Trust adds vertical segmentation aligned with business processes and operational outcomes.
What does this look like in practice?
Instead of assuming that all Level 2 HMIs share the same security posture, we focus on what each system actually supports:
- Production Line A’s HMI has its own protect surface, with access limited to what’s needed to run that line.
- Building Management HMI is isolated – HVAC doesn’t need access to production equipment.
- Quality Control HMI has a separate protect surface, limited to the sensors and databases it needs.
This is where IT and OT must collaborate. Defining protect surfaces requires:
- OT knowledge of which assets are critical and how they depend on each other
- IT expertise to apply controls and monitoring
- A shared lens to align security with operational goals
The result?
Not IT security. Not OT security. Integrated security that protects the business.
The protect surface advantage
Protect surfaces cut vertically across Purdue layers, wrapping security around specific business processes.
This approach delivers:
- Limits lateral movement: A breach in one protect surface doesn’t cascade.
- Aligns with business risk: Security focus goes where operational impact is highest.
- Enables gradual implementation: Start small, scale with confidence.
- Facilitates IT-OT collaboration: IT and OT work together toward the same outcome.
The Purdue layers still matter.
They still provide valuable defense-in-depth.
But they need vertical segmentation layered in.
Practical steps toward IT/OT convergence
Adopting Zero Trust 2.0 in OT is not just a technical – it’s organizational.
It demands structured collaboration.
1. Identify critical protect surfaces – together
Bring IT and OT into the same room.
Map the business processes that matter most.
Ask:
- What would be the business impact if this process failed?
- Who needs access to these systems, and why?
- What’s the acceptable security posture for this level of business risk?
This reveals blind spots.
It also builds a shared language – the foundation of trust.
This is also the first step in Zero Trust methodology.
Make Zero Trust Feel Clear, Not Complicated
Step into a world where cybersecurity finally makes sense. Our Dictionary helps you cut through the noise, understand the language, and feel confident in every conversation—no matter your expertise level.
2. Define realistic security requirements
For each protect surface, define what’s possible – together:
- From the OT: What are the operational constraints? Maintenance windows? Safety factors?
- From the IT: What controls can be enforced? What can be monitored? How fast can we respond?
This isn’t about perfect security on day one.
It’s about building a workable baseline, and improving over time.
Moving forward: together
The IT/OT divide made sense when they were truly separate.
That world is gone.
AI, cloud, remote access, and predictive maintenance have fused the domains.
Neither can succeed alone.
Zero Trust 2.0 for OT accepts that reality.
It builds on Purdue’s horizontal model and adds vertical protect surfaces – aligned to what the business actually runs on.
But it only works if IT and OT collaborate by design.
The tech challenges are solvable.
The cultural ones – that’s where the real work is.
IT must understand: availability is everything in OT.
OT must accept: security can’t be optional in a connected world.
Communication is the unlock.
Not just between machines – but between the people who run them.
When IT and OT share a language and a goal, you get security that protects operations – without stopping them.
The Real Question
It’s not: “Will IT and OT converge?”
They already are.
It’s: “Will you manage that IT/OT convergence by design – or react after damage is done?”
Zero Trust on the Purdue Model gives you the framework.
Collaboration gives you execution.
Together, they secure the factory floor in a connected world.
The future of OT security?
It’s not IT. It’s not OT.It’s both. Together.
FAQ
No. It builds on the Purdue Model. Horizontal segmentation still matters – Zero Trust adds vertical protect surfaces around business processes.
Because OT prioritizes availability and safety. IT controls can break things. Zero Trust for OT adapts to those constraints.
Start by identifying critical business processes, then define protect surfaces around them. This creates focus and shared understanding between IT and OT.
Security is aligned to business outcomes – not just tech silos. IT and OT teams focus on shared goals.
No. Start small. Protect surfaces can be implemented gradually, starting with the most critical processes. Then scale.


