OT security can feel like a black box to those in IT: complex, inflexible, and a little mysterious. There is often an assumption, particularly among those in networking, that because OT systems have IP addresses, they must operate just like IT systems.
In some ways, that is true. But there are important differences that make IT and OT fundamentally distinct.
First things first: what is OT security?
Operational Technology (OT) refers to the hardware and software that control physical systems like factory equipment, power grids, or hospital machines. Unlike IT, which focuses on data access and user services, OT is about delivering physical products and tangible services.
If IT fails, most companies can still function. If OT fails, the consequences can vary from halted production, to even physical damage and life-threatening situations. Think marine vessels or even hospitals, where systems like oxygen generators, insulin pumps, elevators and heart-lung machines fall under OT.
Curious about OT’s Hidden Cyber Risks? Check out this episode of Threat Talks, where we explore how airports, hospitals, ports, and even water systems can be compromised.
IT versus OT security
When talking about the differences between IT and OT, we recognize that they prioritize system values differently. In IT, the standard framework is the CIA triad: Confidentiality, Integrity, and Availability. OT, however, follows the SRP triad (Safety, Reliability & Performance). The further you move from IT to OT to ICS (Industrial Control Systems), the more important the SRP triad, and the less important the CIA triad becomes.
Another major difference between IT and OT lies in device lifecycles. IT devices typically last 3 to 5 years. OT devices, on the other hand, are expected to run for 25 to 30 years. The upfront investment for OT equipment is enormous, and that’s before factoring in the time and effort required to bring a new production line online. Think of new processes, procedures, connectivity requirements, training, and more.
As a result, IT environments are fast-moving and constantly evolving. Stability is nice to have, but not strictly necessary. In contrast, OT environments are built for long-term, uninterrupted operation: think 24/7/365 for decades.
The challenges of securing OT
OT vendors live and breathe reliability and consistency. Anything that might affect the stability or performance of their systems is typically off-limits.
In many cases, it’s not just about what you’re prohibited from doing: it’s about a strict list of actions you are allowed to take. Straying from that list can void warranties, break support agreements, and shift liability.
Even when changes are permitted, like installing security software, modern solutions often aren’t compatible. Many OT devices still rely on legacy operating systems that aren’t supported by today’s security tools.
It’s important to remember that most OT systems in use today were designed 20 or more years ago, at a time when security simply wasn’t a priority. Concepts that are second nature in IT now (such as proper authentication, encryption, and automated updates) weren’t even part of the conversation back then.
What this means for securing OT environments
Securing OT environments isn’t as simple as applying traditional IT security tools. For example, installing an EDR solution directly on OT devices is usually not allowed. These tools can interfere with how the devices function, voiding vendor warranties and compromising safety or availability.
Most OT vendors also prohibit anything that sits inline with communication paths, such as Intrusion Prevention Systems, because any disruption could impact reliability. As a result, OT security tools are typically deployed in a TAP (test access point) configuration. They monitor traffic passively and raise alerts, but can’t block threats in real time. It’s up to OT security teams to investigate and respond manually.
There’s another layer of complexity: many OT protocols (like Modbus, DNP3, and BACnet) are decades old and lack basic security features like authentication and encryption. This makes them vulnerable to spoofing, interception, and manipulation.
Most OT networks are also flat, meaning all devices share the same network segment with little or no isolation. Once an attacker breaches one device, moving laterally becomes trivial.
Adding to the challenge, many facilities rely on third-party vendors for remote maintenance. These vendors often use outdated remote access tools, not by choice, but because the OT systems can’t support modern alternatives. And as IT and OT increasingly converge, the old “air gap” is disappearing. That gap once offered a degree of protection. Now, IT threats can move into OT environments, with few traditional defenses like IPS or EDR in place to stop them.
Securing OT, one layer at a time
Securing OT may be challenging, but that doesn’t mean it’s impossible. A structured, layered approach can go a long way.
In order to explain this approach, it might be useful to have an example. Let’s work out OT security for a company that creates products out of apples.
Example: Apple Mania
Apple Mania is a company that buys apples and turns them into all sorts of products. Some of the products they produce are the following:
Food & Beverage Products
- Apple Juice & Cider – Fresh-pressed apple juice, filtered or cloudy, and alcoholic apple cider (hard cider).
- Apple Vinegar – Fermented apple cider vinegar for cooking, health, and cleaning uses.
- Dried Apple Snacks – Dehydrated apple rings or chips, potentially with flavors (cinnamon, honey-glazed, chocolate-coated).
- Apple Jam & Preserves – Apple butter, apple jam, or mixed fruit spreads.
- Apple Sauce – Smooth or chunky, sweetened or unsweetened, for direct consumption or baby food.
- Apple-Based Confectionery – Candied apples, caramel-coated apples, apple fruit leather, or apple gummies.
- Apple Wine & Brandy – Fermented apple wine or distilled apple brandy (e.g., Calvados).
- Apple Powder – Dehydrated apple powder for baking, smoothies, or supplements.
Health & Wellness Products
- Apple Extract for Supplements – Polyphenol-rich apple extract for antioxidant and heart-health supplements.
- Apple Pectin Powder – Pectin extracted from apple peels for digestive health and use as a natural gelling agent.
- Apple Fiber Supplements – High-fiber powder for gut health and diet products.
Cosmetics & Skincare
- Apple-Based Skincare – Apple extract for facial masks, serums, and lotions with anti-aging and brightening properties.
- Apple-Infused Hair Care – Apple cider vinegar shampoos, conditioners, and scalp treatments.
- Apple-Scented Soaps & Candles – Natural apple-based soaps, bath bombs, and scented candles.
Industrial & Eco-Friendly Products
- Apple-Based Bio-Plastic – Apple pulp and fibers for biodegradable packaging and disposable items.
- Apple Waste Biomass for Energy – Fermentation of apple waste to create bioethanol or biogas.
- Apple-Derived Natural Dyes – Apple skins and extracts for textile or cosmetic dyes.
To support this, they’ve built a smart front-end for order processing. Buyers place orders online, and fulfillment happens with minimal human input.
Behind the scenes, Apple Mania’s production facility is complex and broken into multiple phases:
- Intake and storage (with oxygen-controlled environments)
- Quality control (sorting out damaged fruit)
- Washing (removing pesticides)
- Pressing (extracting juice)
- Optimization (repurposing waste for other products)
- Waste management (minimizing discard and powering biomass)
- Packaging (integrated per production line)
- Warehousing (enabling fast delivery)
Each phase includes devices that must be monitored, configured, and controlled. Some systems are tightly integrated, while others operate more independently, but they all work together like a well-coordinated orchestra. The question is: how do you secure such a complex and interconnected OT environment?
Step 1: Know your assets, define your protect surfaces
Zero Trust encourages us to move away from securing individual systems and instead focus on securing DAAS elements: Data, Assets, Applications, and Services.
In the case of Apple Mania, several phases of production can be treated as standalone DAAS elements, each representing a protect surface, which is a clearly defined area that must be secured independently:
- Apple storage, which operates independently from other processes
- Quality control, which filters apples and stores output separately
- Washing, which prepares apples post-quality control and can hold them before further processing
- Pressing, which converts apples to juice and stores juice in large containers
- Waste management, which processes pressing byproducts in batches
- Packaging, which packages juice from storage for distribution
- Warehousing, which stores finished products with consideration for shelf life
Each of these is a logical boundary with specific inputs, outputs, and risks. By identifying these seven protect surfaces, Apple Mania can begin to apply targeted security controls tailored to each zone’s needs and functions.
Step 2: Transaction flows
In a traditional OT environment, all protect surfaces typically share the same network. This means if an attacker breaches one OT device, lateral movement allows access to others.
To prevent this, follow three key steps to control interactions between protect surfaces:
- Access to the OT environment should be limited to pre-approved and explicitly defined flows. This means placing a firewall between IT and OT that performs packet-based inspection with IPS functionality.
- Access from one protect surface to another should also be limited to pre-approved flows, enforced by firewalls between production lines with IPS enabled.
- Each phase should run on its own physical infrastructure, including separate switches.
These steps provide important protections:
- Access from IT into OT becomes much harder because users need the right identity and location to connect.
- If one protect surface is compromised, moving to another becomes significantly more difficult since they are isolated.
- A failure in physical infrastructure affects only that protect surface.
- Third-party vendors working on one line cannot accidentally disrupt others.
This approach effectively builds a Distributed Control System (DCS), as described in the Purdue model. A DCS is a group of isolated systems controlling a specific process, including HMIs (Human Machine Interfaces), PLCs (Programmable Logic Controllers), and related mechanical devices like sensors and pumps.
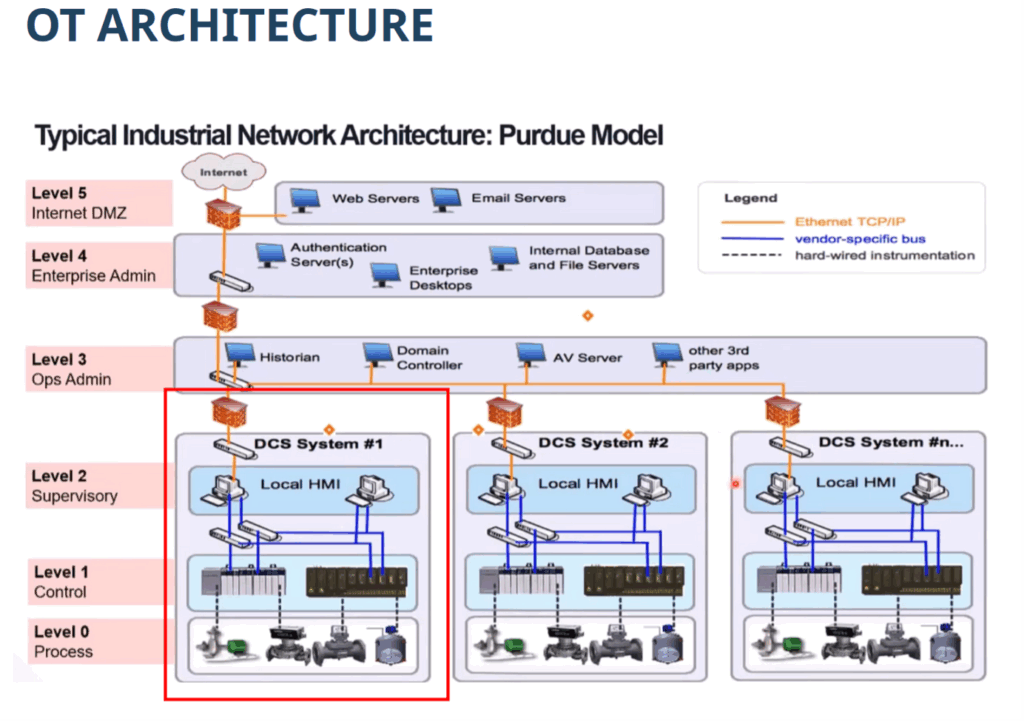
One issue not fully addressed is lateral movement within a single protect surface. The question is whether or not it’s worth it to resolve this issue. After all, when any one part of a DCS system or protect surface is compromised, the entire line cannot run and needs to be shut down anyway.
Step 3: Controls & architecture
With protect surfaces and transaction flows defined, we have a clear map of each production line and its interactions, though no infrastructure changes have been made yet. At this stage, it is all about defining scope and requirements.
Requirements for OT systems often mirror those in IT, but OT vendors may restrict certain controls. For example, most OT systems do not allow installing antivirus, EDR, or XDR solutions. You can specify these as required controls, but their implementation might not be possible today, creating a gap between requirements and reality.
Even if you cannot implement some controls now, documenting them matters. Future opportunities might allow you to close these gaps.
Using your list of required controls, such as disk encryption, SSL inspection, hardened hardware, and centralized logging, you can start shaping the architecture for each protect surface or production line.
This might involve redesigning physical infrastructure or repositioning tools. Sometimes immediate implementation is not feasible, but that is okay. The goal is to identify improvements possible with existing resources before investing in new hardware or software.
The key is to place all required controls thoughtfully to achieve the desired security outcomes.
Step 4: Policy enforcement
Once controls are in place, it’s time to configure them to enforce the defined policies. Having an inventory of OT devices helps, as it lets you create firewall rules based on device types rather than IP addresses.
For example, firewall policies can allow monitoring of PLCs that control juice pack fill rates, without granting access to other PLCs. This creates more fine-grained, dynamic policies that adapt automatically to the live environment and stay up to date.
Communication Protocols
The toughest challenge in OT security is controlling messages shared via protocols like S7 or Modbus. Machine learning can help by learning normal commands and creating allowlists.
But problems arise when the allowlist does not include all necessary operations. For instance, if a shutdown was never part of the learning period, how would you allow a planned maintenance stop? If both start and stop commands are allowed, how do you detect abuse, such as repeatedly starting and stopping the line, which damages equipment and wastes production?
While this kind of fine control is ideal, it often proves expensive and time-consuming for limited gains. Other simpler, lower-cost steps usually provide a bigger security impact with less effort.
Step 5: Monitor & maintain
Now that you have updated your environment to become more resilient and that you have introduced an anti-fragile architecture, it is time to ensure that the environment is monitored and maintained. Logs generated by your controls should be reviewed, ideally through automated systems.
Any changes in the production line or protect surfaces must be checked against earlier requirements, with evidence provided to confirm continued alignment with your designed architecture.
This is also the part where the inspection of OT messages can play a role. While proactive, in-line prevention can be challenging, monitoring OT message logs for alerts is more feasible. It allows you to detect issues early without disrupting critical processes due to incomplete definitions.
The OT security bottom line
Securing OT environments is complex, but by breaking it down step-by-step, it becomes manageable. Understanding your assets, defining clear protect surfaces, setting realistic controls, enforcing precise policies, and maintaining continuous monitoring all build a strong defense.
While OT security has unique challenges compared to IT, taking a layered, thoughtful approach helps protect critical systems without disrupting operations. With the right strategy, you can confidently safeguard your OT environment today and adapt as new technologies and threats emerge.


